Kubernetes networking facilitates the transfer between containerization components. The main benefit of this networking model is that it eradicates the need to outline ports between hosts and containers. Nevertheless, configuring a Kubernetes networking model is never a straightforward task. This article will study what Kubernetes networking is, explore conventional implementations, and learn essential Kubernetes networking modifications.
What Is Kubernetes Networking Model?
Kubernetes (k8s) is an open-source container orchestration program. You can utilize it to automate deployments, updates, and services of containers on-premises or in the cloud. With k8s, you can handle containerized workloads beyond complicated infrastructures without bothering about operating systems or situations.
Kubernetes networking model is a model that k8s applies to facilitate interaction between its elements. It is based on a horizontal network composition and does not need to map ports within hosts and containers. Although Kubernetes networking can be a dare to set up, it is a necessary part of any k8s process and one that you want to know for successful deployment.
Kubernetes networking types
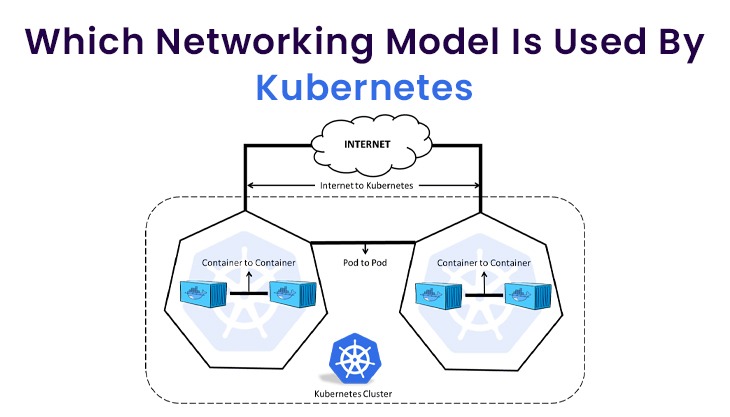
We have four different Kubernetes networking Types:
1) Container-to-Container networking
2) Pod-to-Pod networking
3) Pod-to-Service networking
4) Internet-to-Service networking
Container-to-Container Networking
A high-level illustration of networking represents a device or virtual machine communicating instantly with Ethernet equipment. However, in actuality (at least with Linux), every process on your computer shares inside a network namespace.
This namespace creates a consistent networking heap with its own network devices, firewall commands, and maps. When you operate a process, it is authorized by default to your source network namespace. This renders the process with visible access.
In Kubernetes, your containers are classified into pods, all with a distributed namespace. Inside this pod, all containers have identical port and IP address and port space. To communicate, containers in a pod can use localhost since all function in the equivalent namespace. If containers in separate pods need to participate, you are applying the pod-to-pod networking process outlined underneath.
Pod-to-Pod Networking
Pod-to-pod networking can happen for pods inside the same node or beyond nodes. All of your nodes have a classless inter-domain routing (CIDR) block. This block is a determined set of unique IP addresses that are authorized to pods within that node. This ensures that each pod is equipped with a unique IP, notwithstanding which node it is in.
When pods require transfer, a virtual ethernet device (VED) or a veth pair is employed to attach the pods. Veth pairs are joined network interfaces that are scattered over namespaces. One of the pairs is committed to the root namespace and the other to the pod namespace. Then, the VED is utilized as an intermediary agent within the two namespaces.
Pod-to-Service Networking
Kubernetes is intended to allow pods to be substituted dynamically, as required. This symbolizes that pod IP addresses are not long-lasting except special precautions are practised, such as stateful applications. To address this problem and guarantee that information with and among pods is affirmed, Kubernetes uses services.
Kubernetes services control pod states and empower you to track pod IP addresses over terms. These services abstract pod addresses by specifying a single virtual IP (a cluster IP) to collect pod IPs. Then, any traffic addressed to the virtual IP is assigned to the associated pods.
This service IP allows pods to be produced and consumed as needed without influencing overall information. It also enables Kubernetes services to serve as in-cluster load balancers, distributing traffic as required amongst associated pods.
Internet-to-Service Networking
The ultimate networking situation that is demanded most utmost deployments is within the Internet and services. Whether you are adopting Kubernetes for internal or external applications, you frequently need Internet connectivity. This connectivity enables users to obtain your services and shared teams to collaborate.
When setting up an external entrance, there are two methods you require to apply — egress and ingress. You can set up specific policies with whitelisting or blacklisting to direct traffic into and out of your network.
Conclusion
Kubernetes technology empowers you to configure connections inside your k8s network. It is based on a smooth network structure, excluding the need to map ports among hosts and containers. However, to implement this network model, you must use third-party devices of the open-source or advanced variety.
Additionally, when setting up your Kubernetes technology, you need to consider several networking aspects that you will not find in traditional networking. These involve container-to-container networking, pod-to-pod networking, pod-to-service networking, and Internet-to-service networking. Be sure to design your network thoroughly because misconfiguration can result in vulnerabilities.













Post Comments